dell6400note
Intern
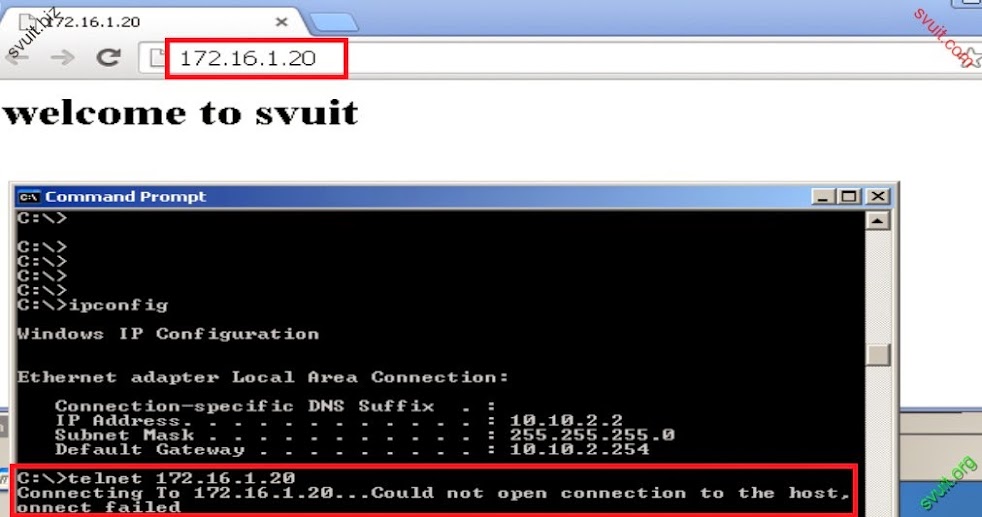
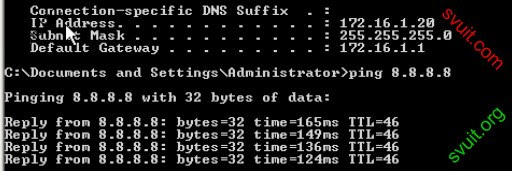
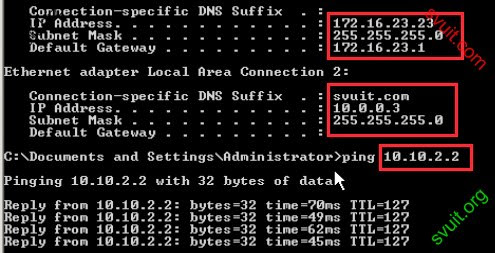
@ROOT: Mình đang làm bài Lab liên quan đến VPN client, còn vướng đoạn NAT các port để cho phép VPN client kết nối qua WAN1, và POOL VPN có thể kết nối tới VLAN_SRV như topo dưới đây, bạn chỉ giúp mình nhé:
I. TỔNG QUAN:
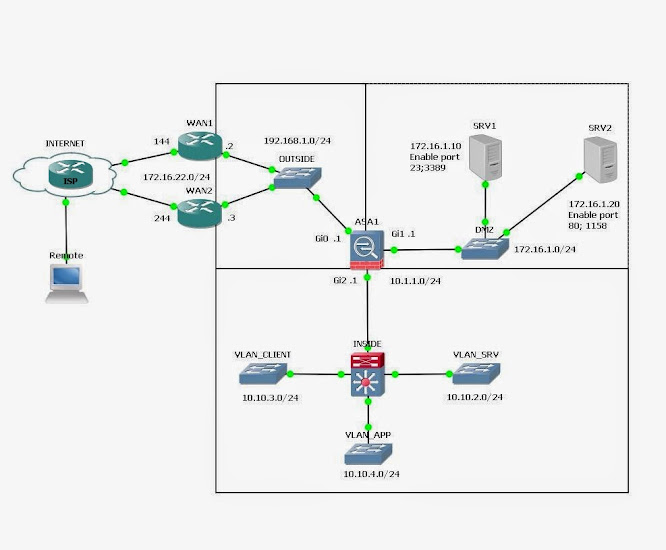
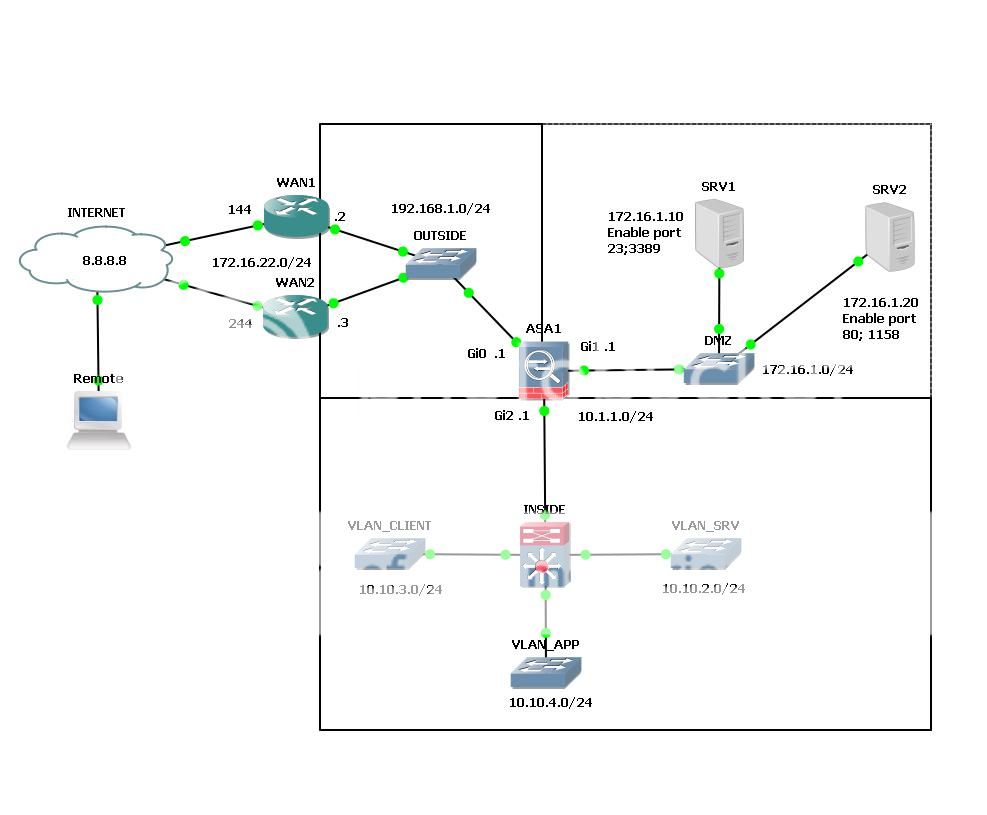
1. Mô hình:
2. Yêu cầu:
Mạng INSIDE:
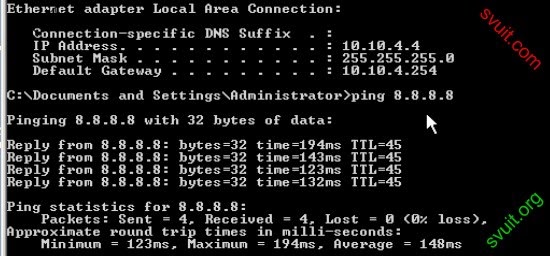
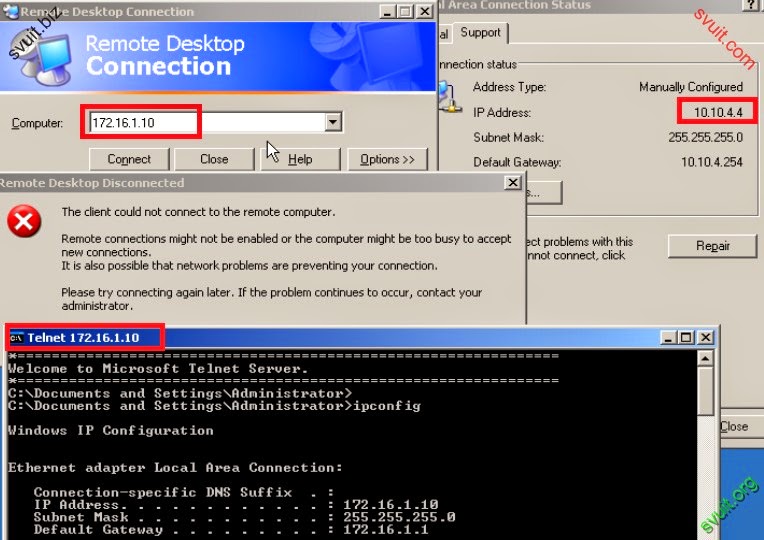
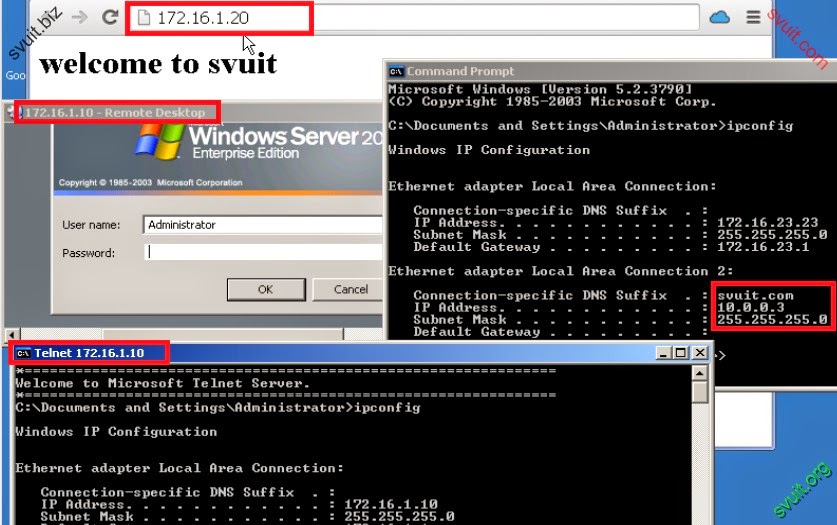
VLAN_CLIENT; VLAN_APP kết nối dc INTERNET, chỉ telnet được SRV1 vùng DMZ.
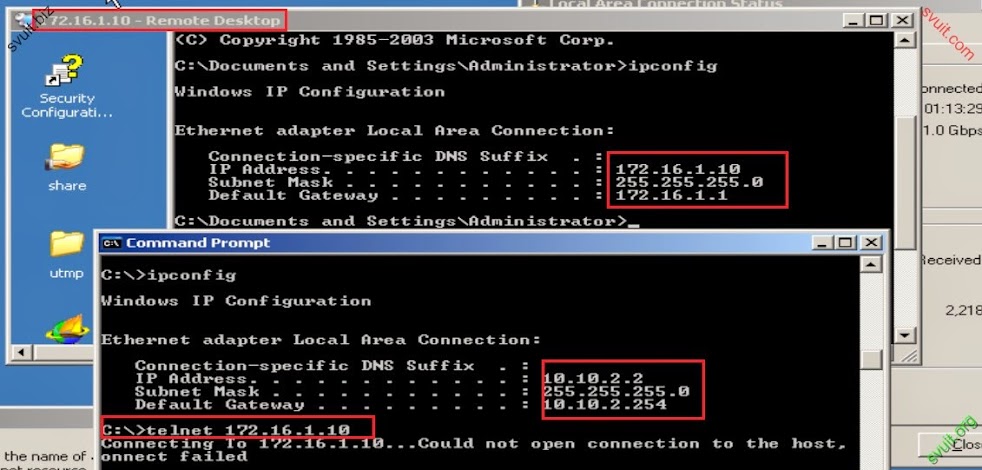
VLAN_SRV: không kết nối INTERNET, chỉ giao tiếp với port 80 của SRV2, port 3389 của SRV1 trên vùng DMZ.
Mạng DMZ:
Kết nối được INTERNET và public các port 23 tại SRV1; port 1158 tại SRV2 qua WAN1
Mạng OUTSIDE:
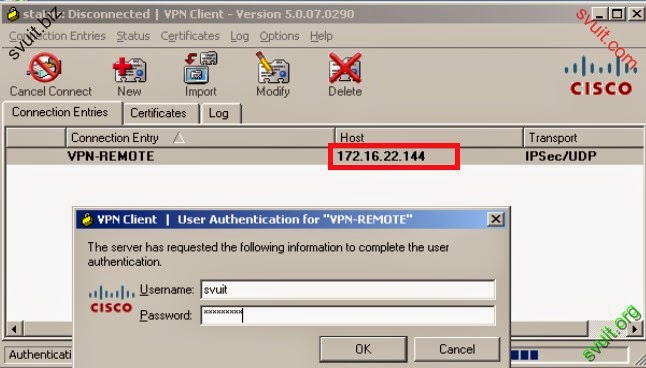
Mở VPN client
Nat mạng INSIDE ra INTERNET
Forward các port 23 của SRV1, 1158 của SRV2
WAN1:
Đường chính ra INTERNET
Cho phép VPN client kết nối
WAN2:
Đường dự phòng ra INTERNET
Nat port public ra INTERNET
REMOTE:
Kết nối được các port của DMZ đã public
Kết nối VPN client có thể truy cập VLAN_SRV
II. TRIỂN KHAI:
1. WAN1:
interface FastEthernet0/0
description Connect to INTERNET
ip address 172.16.22.144 255.255.255.0
ip nat outside
!
interface FastEthernet0/1
description Connect to OUTSIDE ASA
ip address 192.168.1.2 255.255.255.0
ip nat inside
standby priority 110
standby 1 ip 192.168.1.254
standby 1 preempt
standby 1 track FastEthernet0/0
!
ip nat inside source list 1 interface FastEthernet0/0 overload
ip nat inside source static udp 192.168.1.1 10000 interface FastEthernet0/0 10000
ip nat inside source static udp 192.168.1.1 50 interface FastEthernet0/0 50
ip nat inside source static esp 192.168.1.1 interface FastEthernet0/0
ip nat inside source static udp 192.168.1.1 500 interface FastEthernet0/0 500
ip nat inside source static udp 192.168.1.1 4500 interface FastEthernet0/0 4500
ip classless
ip route 0.0.0.0 0.0.0.0 172.16.22.1
ip route 10.1.1.0 255.255.255.0 192.168.1.1
ip route 172.16.1.0 255.255.255.0 192.168.1.1
!
access-list 1 permit any
!
end
2.WAN2:
!
interface FastEthernet0/0
description Connect to INTERNET
ip address 172.16.22.244 255.255.255.0
ip nat outside
duplex auto
speed auto
!
interface FastEthernet0/1
description Connect to OUTSIDE ASA
ip address 192.168.1.3 255.255.255.0
ip nat inside
duplex auto
speed auto
standby 1 ip 192.168.1.254
standby 1 preempt
standby 1 track FastEthernet0/0
!
ip nat inside source list 1 interface FastEthernet0/0 overload
ip classless
ip route 0.0.0.0 0.0.0.0 172.16.22.1
ip route 10.1.1.0 255.255.255.0 192.168.1.1
ip route 172.16.1.0 255.255.255.0 192.168.1.1
no ip http server
!
access-list 1 permit any
!
end
3.FW:
!
interface GigabitEthernet0
description Connect to OUTSIDE
nameif OUTSIDE
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1
description Connect to DMZ
nameif DMZ
security-level 50
ip address 172.16.1.1 255.255.255.0
!
interface GigabitEthernet2
description connect to INSIDE
nameif INSIDE
security-level 100
ip address 10.1.1.1 255.255.255.0
!
ftp mode passive
object network VLAN_CLIENT
subnet 10.10.3.0 255.255.255.0
object network VLAN_APP
subnet 10.10.4.0 255.255.255.0
access-list VPN-ACL extended permit ip 10.1.1.0 255.255.255.0 10.0.0.0 255.255.255.0
access-list VPN-ACL extended permit ip 10.10.4.0 255.255.255.0 10.0.0.0 255.255.255.0
pager lines 24
mtu OUTSIDE 1500
mtu DMZ 1500
mtu INSIDE 1500
ip local pool VPN 10.0.0.10-10.0.0.20 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network VLAN_CLIENT
nat (INSIDE,OUTSIDE) dynamic 192.168.1.30
object network VLAN_APP
nat (INSIDE,OUTSIDE) dynamic 192.168.1.40
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.1.254 1
route INSIDE 10.10.2.0 255.255.255.0 10.1.1.2 1
route INSIDE 10.10.3.0 255.255.255.0 10.1.1.2 1
route INSIDE 10.10.4.0 255.255.255.0 10.1.1.2 1
!
dynamic-access-policy-record DfltAccessPolicy
!
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set REMOTE esp-3des esp-md5-hmac
crypto dynamic-map MAP 10 set ikev1 transform-set REMOTE
crypto map MYMAP 10 ipsec-isakmp dynamic MAP
crypto map MYMAP interface OUTSIDE
no crypto isakmp nat-traversal
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
!
group-policy REMOTE-VPN internal
group-policy REMOTE-VPN attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN-ACL
default-domain value test.local
address-pools value VPN
username test02 password KhFSDgWxn0rDWqrc encrypted
username test01 password iFBLEO4jejJz4.OK encrypted
tunnel-group REMOTE-VPN type remote-access
tunnel-group REMOTE-VPN general-attributes
default-group-policy REMOTE-VPN
tunnel-group REMOTE-VPN ipsec-attributes
ikev1 pre-shared-key *****
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
!
: end
I. TỔNG QUAN:
1. Mô hình:

2. Yêu cầu:
Mạng INSIDE:
VLAN_CLIENT; VLAN_APP kết nối dc INTERNET, chỉ telnet được SRV1 vùng DMZ.
VLAN_SRV: không kết nối INTERNET, chỉ giao tiếp với port 80 của SRV2, port 3389 của SRV1 trên vùng DMZ.
Mạng DMZ:
Kết nối được INTERNET và public các port 23 tại SRV1; port 1158 tại SRV2 qua WAN1
Mạng OUTSIDE:
Mở VPN client
Nat mạng INSIDE ra INTERNET
Forward các port 23 của SRV1, 1158 của SRV2
WAN1:
Đường chính ra INTERNET
Cho phép VPN client kết nối
WAN2:
Đường dự phòng ra INTERNET
Nat port public ra INTERNET
REMOTE:
Kết nối được các port của DMZ đã public
Kết nối VPN client có thể truy cập VLAN_SRV
II. TRIỂN KHAI:
1. WAN1:
interface FastEthernet0/0
description Connect to INTERNET
ip address 172.16.22.144 255.255.255.0
ip nat outside
!
interface FastEthernet0/1
description Connect to OUTSIDE ASA
ip address 192.168.1.2 255.255.255.0
ip nat inside
standby priority 110
standby 1 ip 192.168.1.254
standby 1 preempt
standby 1 track FastEthernet0/0
!
ip nat inside source list 1 interface FastEthernet0/0 overload
ip nat inside source static udp 192.168.1.1 10000 interface FastEthernet0/0 10000
ip nat inside source static udp 192.168.1.1 50 interface FastEthernet0/0 50
ip nat inside source static esp 192.168.1.1 interface FastEthernet0/0
ip nat inside source static udp 192.168.1.1 500 interface FastEthernet0/0 500
ip nat inside source static udp 192.168.1.1 4500 interface FastEthernet0/0 4500
ip classless
ip route 0.0.0.0 0.0.0.0 172.16.22.1
ip route 10.1.1.0 255.255.255.0 192.168.1.1
ip route 172.16.1.0 255.255.255.0 192.168.1.1
!
access-list 1 permit any
!
end
2.WAN2:
!
interface FastEthernet0/0
description Connect to INTERNET
ip address 172.16.22.244 255.255.255.0
ip nat outside
duplex auto
speed auto
!
interface FastEthernet0/1
description Connect to OUTSIDE ASA
ip address 192.168.1.3 255.255.255.0
ip nat inside
duplex auto
speed auto
standby 1 ip 192.168.1.254
standby 1 preempt
standby 1 track FastEthernet0/0
!
ip nat inside source list 1 interface FastEthernet0/0 overload
ip classless
ip route 0.0.0.0 0.0.0.0 172.16.22.1
ip route 10.1.1.0 255.255.255.0 192.168.1.1
ip route 172.16.1.0 255.255.255.0 192.168.1.1
no ip http server
!
access-list 1 permit any
!
end
3.FW:
!
interface GigabitEthernet0
description Connect to OUTSIDE
nameif OUTSIDE
security-level 0
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1
description Connect to DMZ
nameif DMZ
security-level 50
ip address 172.16.1.1 255.255.255.0
!
interface GigabitEthernet2
description connect to INSIDE
nameif INSIDE
security-level 100
ip address 10.1.1.1 255.255.255.0
!
ftp mode passive
object network VLAN_CLIENT
subnet 10.10.3.0 255.255.255.0
object network VLAN_APP
subnet 10.10.4.0 255.255.255.0
access-list VPN-ACL extended permit ip 10.1.1.0 255.255.255.0 10.0.0.0 255.255.255.0
access-list VPN-ACL extended permit ip 10.10.4.0 255.255.255.0 10.0.0.0 255.255.255.0
pager lines 24
mtu OUTSIDE 1500
mtu DMZ 1500
mtu INSIDE 1500
ip local pool VPN 10.0.0.10-10.0.0.20 mask 255.255.255.0
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network VLAN_CLIENT
nat (INSIDE,OUTSIDE) dynamic 192.168.1.30
object network VLAN_APP
nat (INSIDE,OUTSIDE) dynamic 192.168.1.40
route OUTSIDE 0.0.0.0 0.0.0.0 192.168.1.254 1
route INSIDE 10.10.2.0 255.255.255.0 10.1.1.2 1
route INSIDE 10.10.3.0 255.255.255.0 10.1.1.2 1
route INSIDE 10.10.4.0 255.255.255.0 10.1.1.2 1
!
dynamic-access-policy-record DfltAccessPolicy
!
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set REMOTE esp-3des esp-md5-hmac
crypto dynamic-map MAP 10 set ikev1 transform-set REMOTE
crypto map MYMAP 10 ipsec-isakmp dynamic MAP
crypto map MYMAP interface OUTSIDE
no crypto isakmp nat-traversal
crypto ikev1 enable OUTSIDE
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
!
group-policy REMOTE-VPN internal
group-policy REMOTE-VPN attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value VPN-ACL
default-domain value test.local
address-pools value VPN
username test02 password KhFSDgWxn0rDWqrc encrypted
username test01 password iFBLEO4jejJz4.OK encrypted
tunnel-group REMOTE-VPN type remote-access
tunnel-group REMOTE-VPN general-attributes
default-group-policy REMOTE-VPN
tunnel-group REMOTE-VPN ipsec-attributes
ikev1 pre-shared-key *****
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
!
: end
Sửa lần cuối:
Bài viết liên quan
Bài viết mới